Exploration & Exploitation: A Unified Framework for Data Purification & Augmentation in Recommendation Systems
Abstract
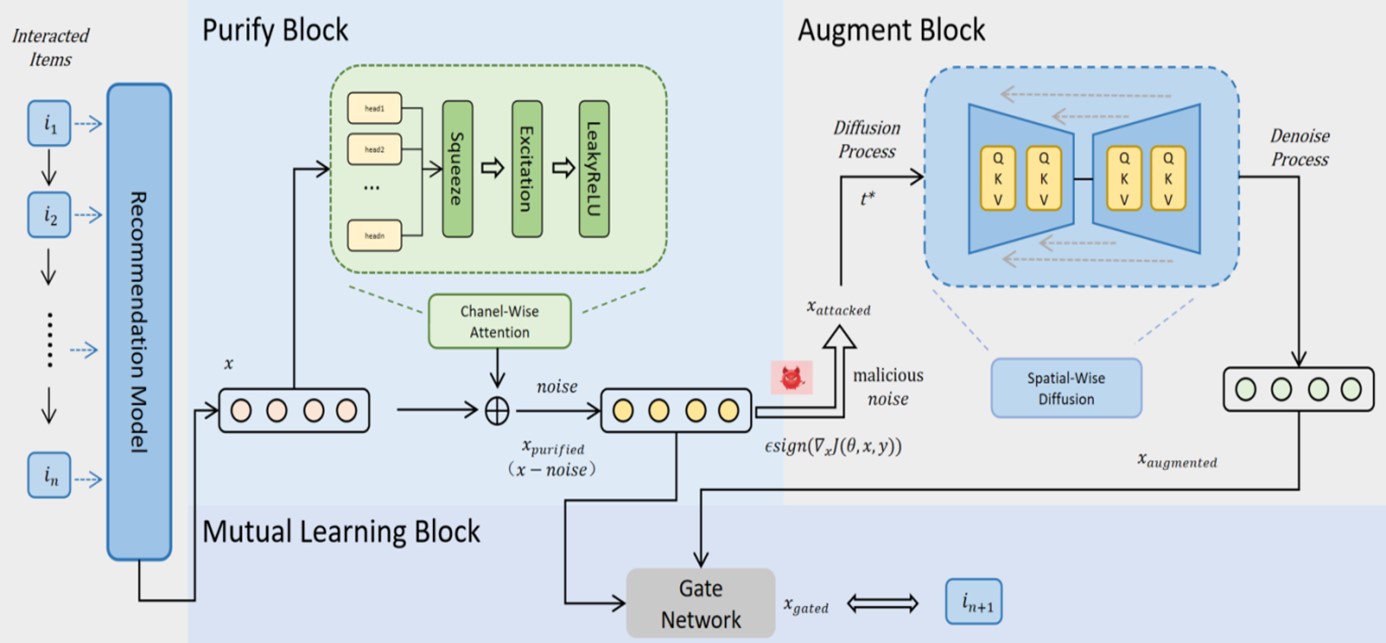
In the context of recommendation scenarios, the utilization of data purification and data augmentation methodologies has demonstrated their efficiency in enhancing the quality of representations. Nevertheless, within an open environment, the constrained nature of interaction data and the diverse range of interaction intentions present formidable challenges, giving rise to insufficient generalization ability and generalization bias in these methodologies. To address this issue, in this paper we introduce Exploitation & Exploration: A Unified Framework for Data Purification & Augmentation in Recommendation Systems, which not only ensures the precise purification of current data but also delves into potential noisy data for further exploration. To be specific, based on the traditional collaborative filtering method calculating user-item correlation, we first implement an efficient multi-head SENet block to remove potential noise from the interaction data. After this, we deploy a diffusion module to remove the added adversarial noise based on its ability to denoise all kinds of noise. And finally we use mutual-learning method to coordinate two parts' learning. We conducted experiments on three publicly available datasets, evaluating our model against current state-of-the-art algorithms in recommendation robustness tasks. The experimental results validate the effectiveness of our model.
References
[2] Gao, Y., Du, Y., Hu, Y., Chen, L., Zhu, X., Fang, Z., & Zheng, B. (2022). Self-guided learning to denoise for robust recommendation. SIGIR, 1412-1422. https://doi.org/10.1145/3477495.3532056
[3] Bian, Z., Zhou, S., Fu, H., Yang, Q., Sun, Z., Tang, J., Liu, G., Liu, K., & Li, X. (2021). Denoising user-aware memory network for recommendation. RecSys, 400-410. https://doi.org/10.1145/3460231.3471690
[4] Qin, Y., Wang, P., & Li, C. (2021). The world is binary: Contrastive learning for denoising next basket recommendation. SIGIR, 859-868. https://doi.org/10.1145/3404835.3462906
[5] Zhang, Y., Chen, E., Jin, B., Wang, H., Hou, M., Huang, W., & Yu, R. (2022). Clustering-based behavior sampling with long sequential data for CTR prediction. SIGIR, 2195–2200. https://doi.org/10.1145/3404835.3463002
[6] Cao, Y., Zhou, X., Feng, J., Huang, P., Xiao, Y., Chen, D., & Chen, S. (2022). Sampling is all you need on modeling long-term user behaviors for CTR prediction. CIKM, 2974–2983. https://doi.org/10.1145/3340531.3412047
[7] Chen, Q., Pei, C., Lv, S., Li, C., Ge, J., & Ou, W. (2021). End-to-end user behavior retrieval in click-through rate prediction model. CoRR, abs/2108.04468. https://arxiv.org/abs/2108.04468
[8] Zhang, Y., Ai, Q., Chen, X., & Wang, P. (2018). Learning over knowledge-base embeddings for recommendation. CoRR, abs/1803.06540. https://arxiv.org/abs/1803.06540
[9] Fan, S., Zhu, J., Han, X., Shi, C., Hu, L., Ma, B., & Li, Y. (2019). Metapath-guided heterogeneous graph neural network for intent recommendation. KDD, 2478-2486. https://doi.org/10.1145/3293663.3293685
[10] Chen, X., Zhang, Y., Xu, H., Cao, Y., Qin, Z., & Zha, H. (2018). Visually explainable recommendation. CoRR, abs/1801.10288. https://arxiv.org/abs/1801.10288
[11] Li, K., Wang, P., & Li, C. (2022). Multi-agent RL-based information selection model for sequential recommendation. SIGIR, 1622-1631. https://doi.org/10.1145/3404835.3462904
[12] Christakopoulou, K., & Banerjee, A. (2019). Adversarial attacks on an oblivious recommender. RecSys, 322-330. https://doi.org/10.1145/3293663.3293677
[13] Chen, H., Zhou, K., Lai, K. H., Hu, X., Wang, F., Yang, H. (2022). Adversarial graph perturbations for recommendations at scale. SIGIR, 1854-1858. https://doi.org/10.1145/3397271.3401300
[14] Chen, H., & Li, J. (2019). Adversarial tensor factorization for context-aware recommendation. RecSys, 363-367. https://doi.org/10.1145/3293663.3293665
[15] Wu, C., Lian, D., Ge, Y., Zhu, Z., Chen, E., & Yuan, S. (2021). Fight fire with fire: Towards robust recommender systems via adversarial poisoning training. SIGIR, 1074-1083. https://doi.org/10.1145/3404835.3462902
[16] Ilyas, A., Santurkar, S., Tsipras, D., Engstrom, L., Tran, B., & Madry, A. (2019). Adversarial examples are not bugs, they are features. NeurIPS, 125-136. https://doi.org/10.5555/3328779.3328937
[17] Wang, R., Fu, B., Fu, G., & Wang, M. (2017). Deep & cross network for ad click predictions. ADKDD@KDD, 12(1), 12–7. https://doi.org/10.1145/3107323.3107325
[18] Lin, C., Chen, S., Li, H., Xiao, Y., Li, L., & Yang, Q. (2020). Attacking recommender systems with augmented user profiles. CIKM, 855–864. https://doi.org/10.1145/3340531.3411913
[19] Li, S., Kawale, J., & Fu, Y. (2015). Deep collaborative filtering via marginalized denoising auto-encoder. CIKM, 811–820. https://doi.org/10.1145/2806416.2806507
[20] Li, H., Di, S., & Chen, L. (2022). Revisiting injective attacks on recommender systems. NeurIPS.
[21] Huang, H., Mu, J., Gong, N. Z., Li, Q., Liu, B., & Xu, M. (2021). Data poisoning attacks to deep learning based recommender systems. NDSS.

This work is licensed under a Creative Commons Attribution 4.0 International License.
Copyright for this article is retained by the author(s), with first publication rights granted to the journal.
This is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).








1.png)














