Cybersecurity Regulations and Risk Management in the Financial Sector: A Comparative Analysis
Abstract
The financial sector has become a prime target for cyber attackers seeking unauthorized access to sensitive data. As social engineering techniques like phishing and denial of service attacks continue to escalate, greater oversight is required to secure financial institutions. While federal and state regulations in countries such as the United States and the United Kingdom aim to provide consumer protection, the level of cybersecurity implementation varies across nations. This paper explores the regulatory landscape of the financial sector, focusing on the United States, the United Kingdom, and the European Union. It examines the specific protections provided by legislation, such as the Gramm-Leach-Bliley Act, the Sarbanes-Oxley Act, and the General Data Protection Regulation. The study highlights the challenges posed by inconsistent state-level policies and the need for international cooperation to address the growing cyber-attack threat. Furthermore, it emphasizes balancing cybersecurity decision-making and policy implementation to ensure adequate regulation and social freedom. This paper also discusses the critical role of business continuity plans, disaster recovery plans, intrusion detection and prevention systems, and incident response plans in mitigating cyber risks. Finally, it explores the potential of cloud computing as a future research direction for enhancing the security and resilience of the financial sector. This review explores cybersecurity frameworks, risk assessment methodologies, and technological advancements, including cloud computing and intrusion detection systems, to mitigate cyber risks in financial institutions.
References
Bakare, S. S., Adeniyi, A. O., Akpuokwe, C. U., & Eneh, N. E. (2024). Data privacy laws and compliance: A comparative review of the EU GDPR and USA regulations. Computer Science & IT Research Journal, 5(3), 528–543. https://doi.org/10.51594/csitrj.v5i3.859
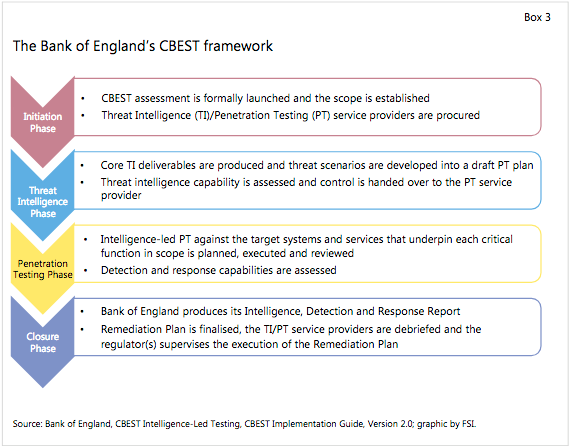
Bank of England. (2021). CBEST: Intelligence-led testing for financial sector firms. https://www.bankofengland.co.uk/-/media/boe/files/financial-stability/financial-sector-continuity/cbest-implementation-guide.pdf
Bank of England. (2023). Prudential regulation authority annual report 2023/24. https://www.bankofengland.co.uk/prudential-regulation/publication/2024/july/pra-annual-report-2023-24
Bischoff, P. (2023, January 9). Internet privacy laws by state: Which US states best protect privacy online? Comparitech. https://www.comparitech.com/blog/vpn-privacy/which-us-states-best-protect-online-privacy/
Benaroch, M. (2018). Real options models for proactive uncertainty-reducing mitigations and applications in cybersecurity investment decision making. Information Systems Research, 29(2), 315–340. https://doi.org/10.1287/isre.2017.0714
Bernard, L., Raina, S., Taylor, B., & Kaza, S. (2021). Minimizing cognitive overload in cybersecurity learning materials: An experimental study using eye-tracking. In L. Drevin, N. Miloslavskaya, W. S. Leung, & S. von Solms (Eds.), Information security education for cyber resilience (pp. 47–63). Springer International Publishing. https://doi.org/10.1007/978-3-030-80865-5_4
Cloud Technology Partners. (n.d.). Cloud adoption in the financial services industry. Retrieved from https://www.cloudtp.com/doppler/cloud-adoption-financial-services-industry/
Crisanto, J. C., Leuterio, C. B., Prenio, J., & Yong, J. (2024). Regulating AI in the financial sector: Recent developments and main challenges (FSI Insights on Policy Implementation No. 63). Bank for International Settlements. https://www.bis.org/fsi/publ/insights63.pdf
De Groot, J. (2024, October 4). What is SOX compliance? What you need to know. Digital Guardian. https://digitalguardian.com/blog/what-sox-compliance
Darem, A. A., Alhashmi, A. A., Alkhaldi, T. M., Alashjaee, A. M., Alanazi, S. M., & Ebad, S. A. (2023). Cyber threats classifications and countermeasures in banking and financial sector. IEEE Access, 11, 125138–125158.
Deutsche Bank. (2025). Business continuity program. https://www.db.com/company/en/business-continuity-program.htm
Ebert, N., Schaltegger, T., Ambuehl, B., Schöni, L., Zimmermann, V., & Knieps, M. (2023). Learning from safety science: A way forward for studying cybersecurity incidents in organizations. Computers & Security, 103, 103435. https://doi.org/10.1016/j.cose.2023.103435
Fagade, T., Maraslis, K., & Tryfonas, T. (2017). Towards effective cybersecurity resource allocation: The Monte Carlo predictive modelling approach. International Journal of Critical Infrastructures, 13(2–3), 152–167. https://doi.org/10.1504/IJCIS.2017.088235
Federal Reserve Bank of New York. (2025). Cyber risk and the U.S. financial system: A pre-mortem analysis. Economic Policy Review. Retrieved from https://www.newyorkfed.org/medialibrary/media/research/epr/2025/EPR_2025_cyber-vulnerability_eisenbach.pdf
Federal Trade Commission. (n.d.). Gramm-Leach-Bliley Act. https://www.ftc.gov/tips-advice/business-center/privacy-and-security/gramm-leach-bliley-act
Financial Conduct Authority. (2024). Regulating the financial sector: Cybersecurity and compliance. Retrieved from https://www.fca.org.uk
First Bank & Trust Company. (2025, January 1). Cybersecurity in 2025: What financial institutions need to know. https://www.firstbank.com/resources/learning-center/cybersecurity-in-2025-what-financial-institutions-need-to-know/
Gordon, L. A., Loeb, M. P., Lucyshyn, W., & Zhou, L. (2015). The impact of information sharing on cybersecurity underinvestment: A real options perspective. Journal of Accounting and Public Policy, 34(5), 509–519. https://doi.org/10.1016/j.jaccpubpol.2015.05.001
Hasan, M., et al. (2022). Qualitative research methods. Tahta Media Group.
Information Commissioner’s Office. (2023). Guide to the General Data Protection Regulation (GDPR). https://ico.org.uk/media/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr-1-1.pdf
Kennedy, E., & Joseph, O. (2024). A review of the impact of intrusion, detection and protection systems (IDPS) in cloud computing environment. International Journal of Modelling & Applied Science Research, 6(9), 215–222. https://cambridgeresearchpub.com/ijmasr/article/view/420/415
Kuner, C., Bygrave, L. A., & Docksey, C. (2020). The EU General Data Protection Regulation (GDPR): A commentary. Oxford University Press. https://doi.org/10.1093/oso/9780198826491.001.0001
Malatji, M., Von Solms, S., & Marnewick, A. (2019). Socio-technical systems cybersecurity framework. Information & Computer Security, 27(2), 233–272. https://doi.org/10.1108/ICS-03-2018-0031
Malatji, M., Marnewick, A., & von Solms, S. (2020). Validation of a socio-technical management process for optimising cybersecurity practices. Computers & Security, 95, 101846. https://doi.org/10.1016/j.cose.2020.101846
Nesterenko, A. (2024, December 22). Banking cybersecurity challenges: Safeguarding financial institutions in 2025. Dashdevs. https://dashdevs.com/blog/cybersecurity-in-banking-main-threats-and-challenges-in-2023/
Ponemon Institute & IBM. (2024). Cost of a data breach report 2024. IBM. https://www.ibm.com/security/data-breach-report
Verizon. (2024). 2024 Data Breach Investigations Report. https://www.verizon.com/business/resources/reports/dbir/
World Economic Forum. (2025). Global cybersecurity outlook 2025. https://reports.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2025.pdf

This work is licensed under a Creative Commons Attribution 4.0 International License.
Copyright for this article is retained by the author(s), with first publication rights granted to the journal.
This is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).






















